

Ethereal, like tcpdump, is a network sniffer. It can capture packets from the network or display saved captures. Capture filters (using tcpdump syntax) determine what is captured and display filters can limit what is displayed. There is also a "folow TCP stream" option that is useful for displaying packets from a TCP session.
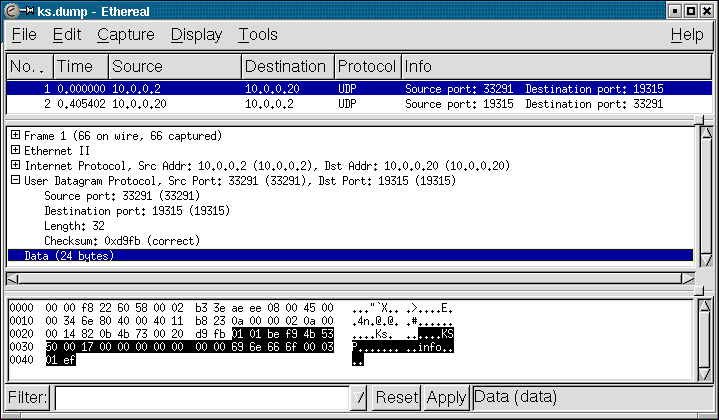
The top frame shows the packets in order of arrival. Source and destination will be host names, IP addresses, or ethernet addresses as available. Protocol can be TCP or UDP, or higher (HTTP, DNS) or lower (ARP, ICMP) protocols. Ethereal can decode a large number of protocols. The info field summarizes the packet contents. For example, for DNS the info field will show the query type and name.
The middle frame shows the packet headers and data. Each header can be expanded to show its fields. For popular protocols, the data section will be decoded as well. This shows all the details of the packet but is easy to read. Here we see the details of the UDP header fields.
The bottom frame shows a hex and ascii dump of the packet. Highlighting a header field in the middle frame will highlight the bytes of that field in the bottom frame. This is where you read the cleartext password ;-)
To impersonate a UDP client, we can mark and save the outgoing packet and then edit it (binary or hex) to leave just the data. Then we use netcat to send our data and receive the response from the server.